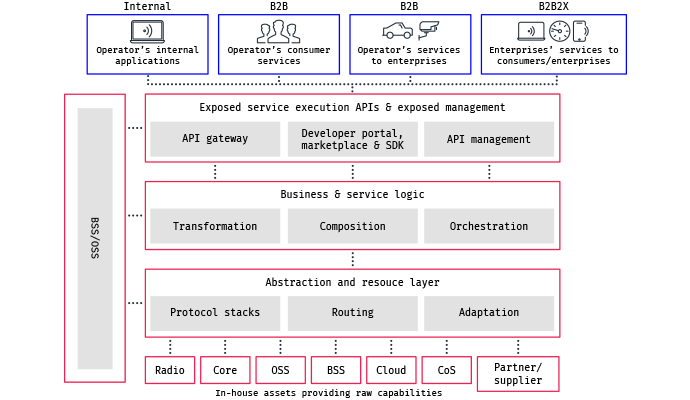
5G presents an opportunity for telecom operators to capture new revenue streams from industrial digitization. In cases such as network-as-a-service (NaaS), network exposure is becoming a reality through the transformation of core telecom network assets into digital assets. With 5G, the dynamic provisioning and scaling of network capacity and resources are available for the first time.
The vision of managing the network-as-a-service in the same way as a developer might manage cloud resources on Azure, AWS, or Google Cloud is happening through a combination of scalable infrastructure and the next generation of digital business support systems (BSS).
The 5G network evolution has opened up an abundance of new business opportunities for communication service providers (CSPs) in verticals such as industrial automation, security, health care, and automotive. To capture the opportunities and leverage their NaaS capabilities, CSPs are deploying automated BSS support systems capable of expanding non-telecom value chains, while supporting new business models through open interfaces.
The world’s digital connections are becoming broader and faster, providing a platform for every industry to boost productivity and innovation. To illustrate the range of possibilities, let’s look at the healthcare industry where connectivity-enabled innovations can make it possible to monitor patients remotely, use AI-powered tools for more accurate diagnoses, and automate many tasks so that caregivers can spend more time with patients.
This technological transformation of the healthcare sector offers numerous opportunities for telecom operators to penetrate new value chains and initiate partnerships that benefit the entire ecosystem. Still it is just one example of how CSPs can partner with a wide range of vertical industries.
Expanding the business models through partners can bring significant benefits and help bring about successful innovation, but inevitably offers less direct control than delivering by themselves in their own controlled environment. It is often said that a business is only as strong as the chain of suppliers it works with.
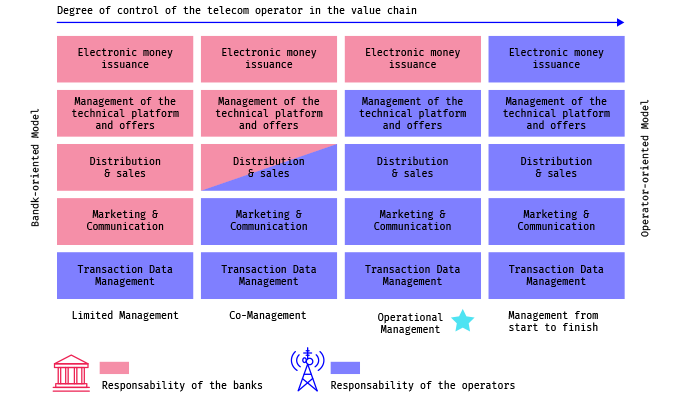
An example of how service delivery chains are becoming complex, and by doing so, becoming more difficult for handling risks, can be exemplified by Uganda’s recent hacker attack on the country’s Mobile Money business that processes phone-based transactions. The mobile money value-chain is made of mobile network operators (MNOs), banks, and end-users, and is a technology that allows people to receive, store, and spend money using a mobile phone.
In the mobile money value-chain, there are blurred risks mostly due to the often-undefined roles of banks and telecommunications companies in financial services, as proven by the recent hack of a gateway that links the bank-to-mobile money transactions. There is a clear line between “banking” and “mobile money” as a standalone business. But the big question is, and when the lines become blurred, is when MNOs expand their services to connect with banks and allow the withdraw of money from regular ATMs.
With digital transformation, telecom risk management initiatives are going through a massive generational shift. Traditionally, telecom value-chain risk management has been heavily supported by analyzing internal events, such as network, OSS/BSS, etc. and optimization models on internally processed data. The shift between just relying on telecom partners and having many vertical partners is pushing in favor of a more vertically integrated technology stack: the cloud. This transition offers all the stakeholders better security and innovation at a lower cost, allowing them to act fast on potential risks.
Not only will 5G driven digital transformation deliver a massive increase in the volume of transactions, but it will also generate a massive diversity of exchangeable events from a variety of partners and services that need to be monitored and analyzed in real-time.
For example, new services that rely on non-face-to-face customer relationships require securing digital identities based on the information exchanged between CSP and their partners. This way, it can be ensured the unique and consistent identification of a subscriber, authentication, and policy assignment based on the identities, whether we are talking about a user or a thing.
At Mobileum, we believe that is the opportunity to leverage the digital transformation data exchange and create the capacity to analyze distributed big data for integrated risk management (IRM) purposes, instead of pursuing a more reactive approach that focuses on finding more data sets and understanding how to use them to address risk. An IRM strategy reduces siloed risk domains and supports dynamic business decision making via risk-data correlations and shared risk processes.
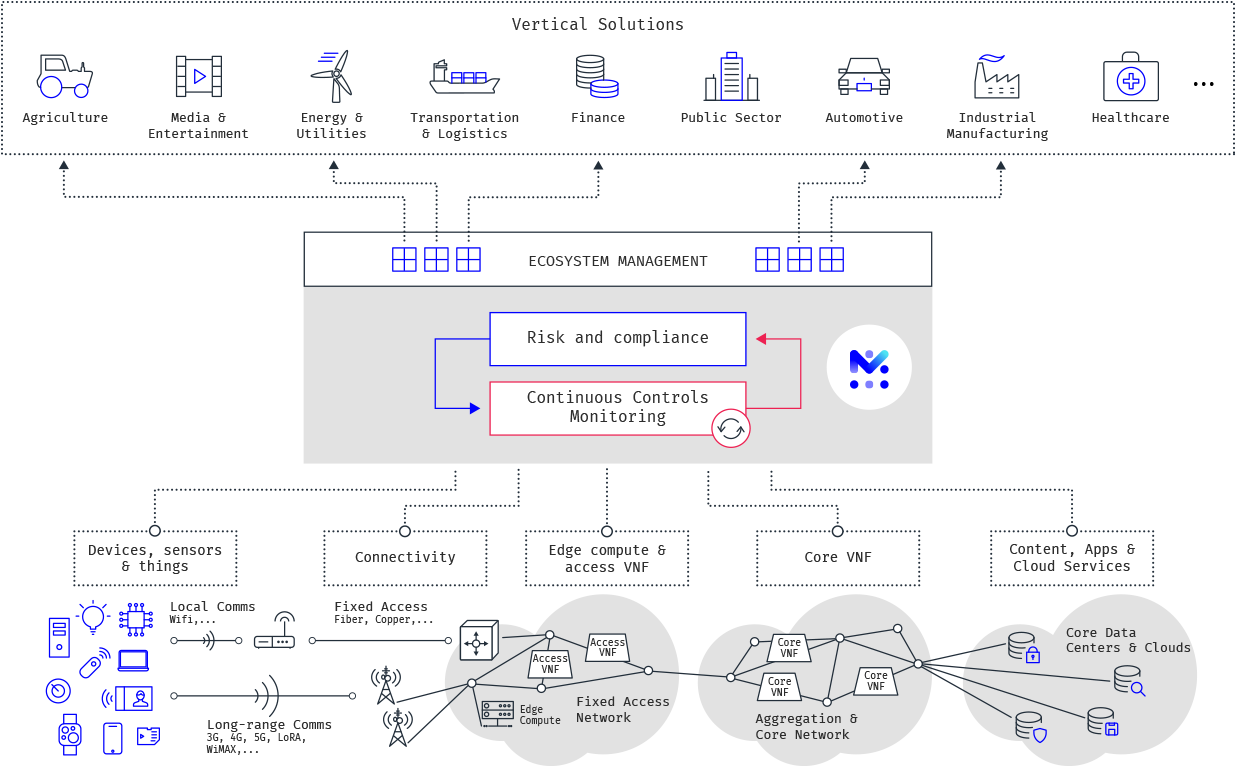
Along with the connectivity platform, CSPs are at a good point to understand and manage a wide scope of risk through a comprehensive view across business units, risk and compliance functions and key business partners, suppliers, and outsourced entities.
The goal should not be to create one big repository that can handle any data set, no matter how large. Instead, it should be to fully automate the linkage among relevant insights from a wide variety of internal and external sources, process that data in various nodes of the supply chain triggering action immediately when possible and adding data to a queue for deeper analysis.
Resilient organizations anticipate risks, develop controls, monitor events, and whenever possible, apply automatic actions to remediate risks. At Mobileum, we believe CSPs will position themselves to lead the emergence of new ecosystems and play their full role in transforming industries and society. Our technology and telecommunications risk management services can assess and protect risk-related issues specific to the telecom industry and assure the industries that are leveraged by connectivity. Currently, we provide a vast stack of solutions that can support the changing imperatives of risk management when it comes to monetization, security, and trust brought by the telco platform economy.
The Mobileum portfolio is unique to assure how our customers build a strong relationship between enterprise risk management and improve its customers’ ability to track risk. At Mobileum, we believe that business resilience and risk management should be tightly linked. By bringing an integrated view of network services, security, and testing and monitoring results, we create a comprehensive view and analysis of risks from fraud, monetization failures, and customer/partner experience while enabling the success of digital transformation.








Give us your comments
Let us know what you thought about this article