Have you ever wondered how artificial intelligence and machine learning are linked to black market smartphones? We open the curtain....
Learn how machine learning and artificial intelligence are being used to curtail the sale of black-market smartphones and prevent point-of-sale fraud
At a FedEx facility in May of 2012, a surprising thing happened. A damaged box, addressed to someone’s home in Rancho Cordova, California – split open, and dozens of new, boxed Verizon iPhones spilled across the floor. A worker at the facility contacted Apple, and it was confirmed that the devices had been stolen and were on their way to being sold on the black market.
In North America, wireless carriers typically subsidize the initial cost of smartphones to lure customers into multiyear voice and data contracts. To obtain a top-notch phone, in other words, subscribers only pay a small fraction of the device’s actual market worth on the day the contract is signed, allowing them to walk out of the store with a phone worth over $1,000, for little or no money down. What many people don’t realize is that fraudsters are taking advantage of this system by using middlemen and mules to obtain high-end devices by paying their accomplices a relatively low fee- about $200 a phone - then selling them online for close to $1,000.
In these “muling” cases, groups of fraudsters recruit, or even physically intimidate, other people into acquiring phones for them. In some cases, the mules are tricked into becoming part of the scam. Typically targeting those in need of quick cash, fraudsters offer these folks a chance to make easy money. Homeless and low-income people with little or no banking history are the primary targets of these schemes. In a typical scenario, this person is sent into a wireless store to sign a contract for a high-end phone in their own name. They leave the shop and are then given cash in exchange for the phone by the fraudster that approached them.
What Telcos have learned the hard way from the evolution of fraud, it is that fraudsters adapt. As soon as one point of attack is shut down, fraudsters will creatively find another way in.
We have seen this happen as “traditional” credit card fraud has migrated to ‘card-not-present’ fraud. Since the introduction of the EMV standard (Europay, MasterCard, and Visa), fraudsters have had a harder time creating counterfeit credit cards. We are now seeing criminals move from using counterfeit credit cards, to using stolen credentials and personal data to commit their crimes. Using another fraud method, but with the same goal in mind, we are now seeing a growing number of purchases being made with gift cards linked to stolen credit card information, providing fraudsters a way to avoid credit card validation checking mechanisms. Often this works, allowing fraudsters to leave the store with a $1000 smartphone, with little to no money down and no intention to pay.
Despite the fact that most CSPs are improving how they verify customer IDs at the point-of-sale through electronic and physical security features embedded into identity documents, or using biometric identification, there is still an abundance of iPhones and other high-end devices suspiciously being sold through online marketplaces such as eBay and Craigslist, among others. Chances are, those phones were purchased with fraudulent gift cards or acquired through other nefarious means.
An innovative approach to Point-of-Sale (POS) Fraud
The push to reduce phone theft at retail stores is causing fraudsters to go online to commit their crimes. But this doesn’t mean that you should look at these two avenues as separate issues requiring separate solutions. During the February GMSA Fraud and Security Group (FASG) event held in Athens, WeDo Technologies presented an innovative approach to POS fraud detection that relies on monitoring online marketplaces to identify suspicious sellers of devices. We then analyze and use this data to alert retailers when these fraudsters try to open an account - before contracts are signed and devices leave the store.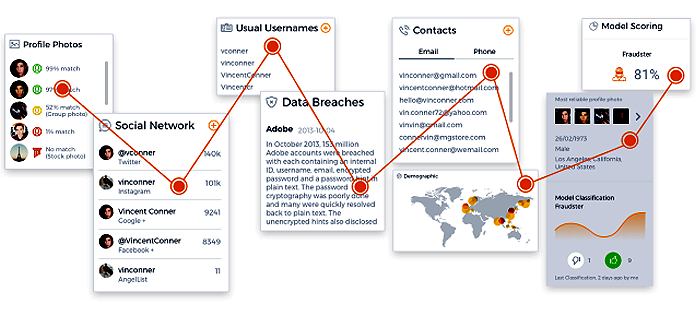
Using publicly available information, WeDo technologies creates a unified digital and physical identity for each user by analyzing the myriad connections between users, locations and anonymized personal information. Besides allowing us to put a face and real name on pseudonyms or nicknames of a seller, the solution effectively creates a hotlist of potential fraudsters. It also collects various attributes that can uncover the various threads relating to a potential fraud ring.
For more information about how we can support your business, please contact us.








Give us your comments
Let us know what you thought about this article