The IoT is composed of an array of devices, software and communications protocols, in a distributed value chain of partners that function as a whole together to create a wide range of new business models delivered to the market.
For many IoT solution providers, the management of third parties and the risks of the IoT value chain have become a boardroom issue. Principally because physical, operational, cyber, financial, and reputational risks are now extending well beyond the traditional boundaries of their organization. IoT solution providers are only as protected and trusted as their weakest partner in their value chain - the proverbial “weakest link.”
To get the right risk management strategy in place, all devices, systems, networks, partners and business models should be viewed holistically with associated requirements and risks in mind.
Properly implemented, assurance by design will guarantee that IoT will have sweeping impacts on the way the world works and lives while minimizing the risks of it.
Over the last several years, IoT has become the innovation core for CSPs, and as a result cybercriminals and fraudsters have broadened their attack targets and fraud activities to better exploit this “multi-partner ecosystem” and take advantage of the unprotected areas from each of stakeholders.
The challenge of understanding the glue along the value chain
The problem with assuring IoT deployments according to traditional risk management governance and strategy is that it largely fails, because the key auditing functionalities are being relegated to isolated selections of tactical technologies, management features and operations procedures along the value chain.
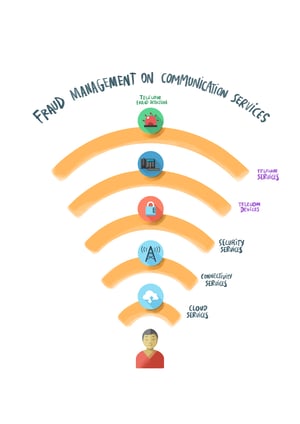
Every day the level of sophistication and organization among fraudsters increases. Gone are the days when a simple set of rules built on top of the OSS/BSS data would be enough for CSPs to stop revenue leakages from telecom fraud. For many years CSPs used to focus primarily on events monitoring within clear organizational boundaries and business support systems. Now though this is changing as CSPs move up the value chain and position themselves as IoT service providers in order to properly monetize IoT opportunities.
As such, when it comes to the CSP’s value proposition for IoT, it is shifting toward an ecosystem-driven model that is no longer just about connectivity, but more about partner management, shared customers and shared revenues. This in turn brings new risks emerging from the many stakeholders.
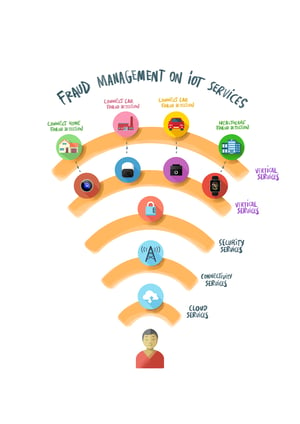
As CSPs release new services outside of their traditional communications portfolio, IoT adds the availability of real-time data and increases the number of customer interactions. This results in a better customer experience, increasing retention, and also allows for a 360º view of the customer for risk management purposes (such as fraud). The analysis of the new data streams increases the understanding of risks and the customer base, which can lead to the assurance of the next generation of products and services. Despite technology to support the IoT being deployed horizontally, a fully integrated risk management strategy may need to go vertically. Protecting the business can only rely on understand things from the vertical markets that they address.
What we’ve seen up to now is that all too frequently IoT risk management concepts and strategies remain as just a concept. They are also forever hampered with biased meanings set by marketing and sales teams from niche vendors such as security companies. Many times this results in an excessive focus on monitoring devices as primary elements for risk management decisions, which fails to deliver complete or adequate risk management, detection, response or predictions for the whole IoT ecosystem.
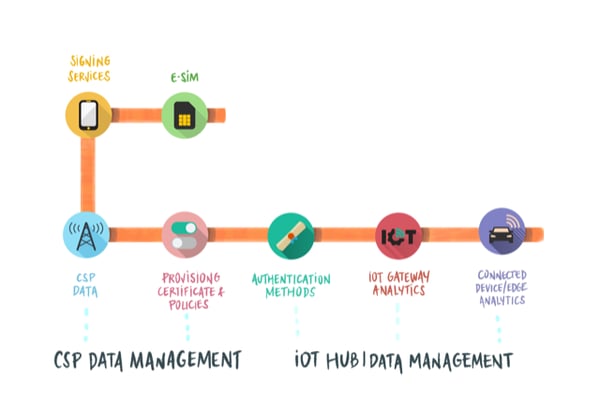
What CSPs need to be aware of is that by releasing new services that fall out of their traditional communications portfolio, the datapoints for risk management no longer remain solely in their own OSS/BSS. All communications data is now the sum of data generated by the relationships of the partners themselves. How they process the data they receive, and how they respond and act upon it, in itself will create effects on how far they are extending the risk management coverage.
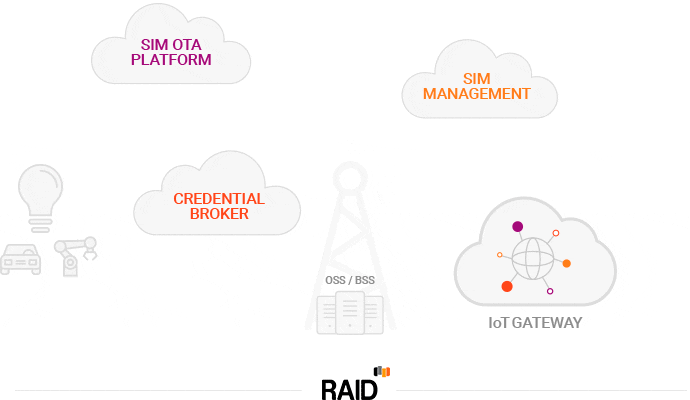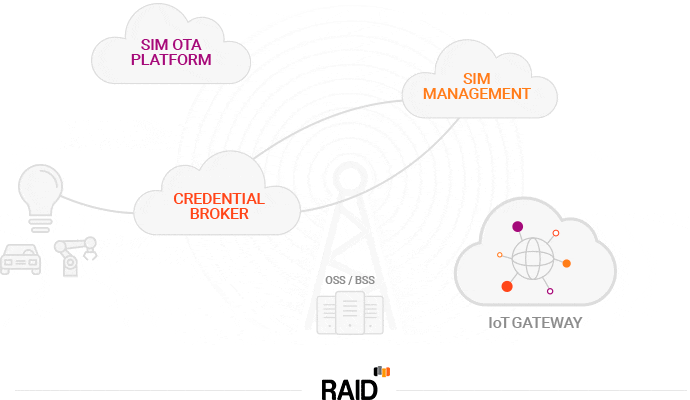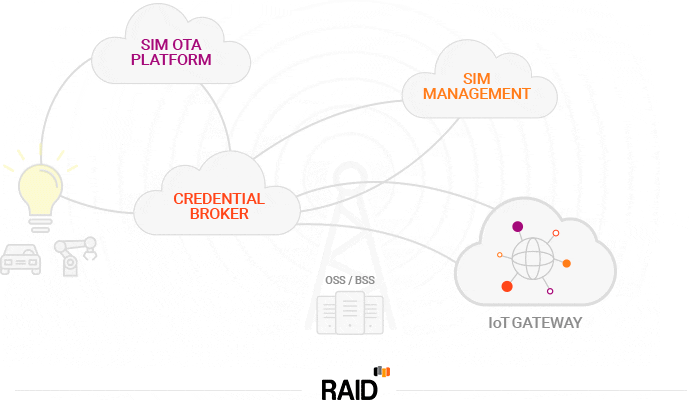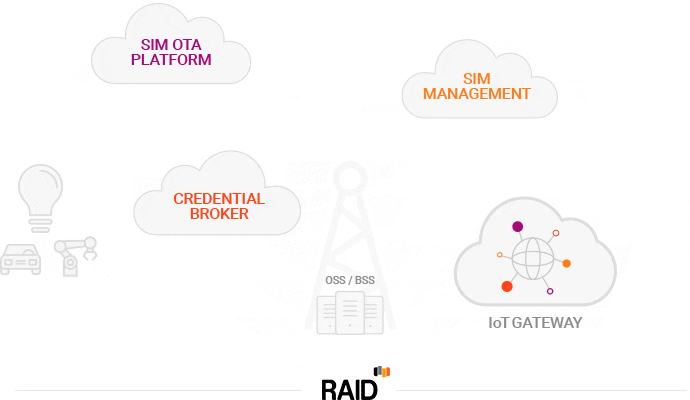
Take for example identity management. Unlike traditional mobile voice services where the user identity is mainly kept in-house with the CSP, with IoT, the role of identity management expands along the value chain. It is no longer just about identifying people and managing their access to services. In the IoT world, identity management must be able to identify devices, sensors and monitors, and then manage their access to sensitive and non-sensitive data along the overall value chain.
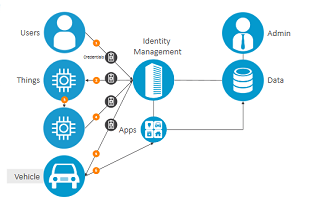
This is an opportunity for influence. If you can connect how these various layers interconnect and behave, then you can start to exploit the glue across these different dimensions for risk management purposes. To build an effective security strategy for the IoT, we first need to understand the business models in place and the value of the data that is being generated. The ability to use data, collected from a variety of locations and sources, can drive risk management decisions making it a key asset in assuring the IoT value chain.
Digital innovation with IoT data is the future of risk management. By taking advantage of emerging technologies such as the IoT, and implementing integrated systems, risk management vendors like WeDo Technologies are able to collect and analyze massive volumes of data from an unlimited number of sources across multiple locations. In this way, we can support our customers to enhance operational processes which improve the timeliness of reporting and utilizing data to drive preventative actions, placing you a step ahead of potential risks.
WeDo Technologies’ IoT Risk Management Practices
The Internet of Things (IoT) is a rapidly expanding space, with new devices, business models and technologies emerging all at the same time. WeDo Technologies IoT risk management framework includes consulting services, software tools, managed services, software deployment and professional services , which can help to design, implement, operate and improve a communication services provider (CSP) with an Internet of Things risk management framework.
If you want to know more on how we can support your IoT risk management strategy, click here, or feel fell free to contact us.








Give us your comments
Let us know what you thought about this article